Chapter 21 Computer Auditing Techniques
LEARNING OBJECTIVES 1. Outline examples of computer auditing techniques such as test data and parallel simulation. |
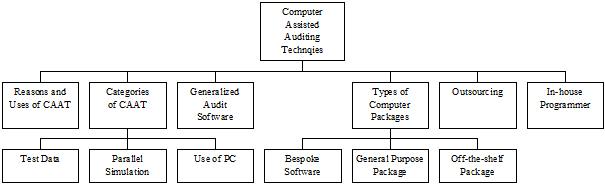
1. Computer Auditing Techniques for Auditing Through the Computer
1.1 Reasons for using CAATs
(Dec 10)
1.1.1 Loss of audit trails (審計跟踪):
(a) when no visible audit trails, e.g. conventional vouching of transactions may not be possible, the transactions input are stored on a log file with no listing of daily or periodic transactions.
(b) Where the audit trail is not available in the design of a computer system, test data may be used to check the processes are being performed properly.
1.1.2 CIS controls – program controls may not be possible to review manually. Using test data or re-performing the processes by programs may be the only method to test the control.
1.1.3 Volume of transactions and output – volume of transaction data is large.
1.1.4 Source documents are often eliminated for a computer-based system, audit evidence is maintained in machine-readable form.
1.1.5 Most of the underlying data in a computerized environment are stored in centralized electronic files.
1.1.6 A computerized information system retrieves data from various sources and processes various transactions simultaneously, transactions are complicated by the summarization of the related details.
1.2 Considerations in the use of CAATs
1.2.1 The following factors should be considered by the auditor: (Dec 14)
(a) The computer knowledge, expertise and experience of the audit team
Auditors should have knowledge of data processing and computer applications together with a detailed knowledge of the audit software and computer files to be used.
(b) Availability of CAATs and suitable computer facilities
The client entity’s computer facility is incompatible or impractical to be used, the auditor may need to plan to use other computer facilities and may need the help of the client’s personnel to provide copies of data files in the required format.
(c) Impracticability of manual audit procedures
It may not be practical for the auditor to perform audit procedures manually if the computer system does not produce hard-copy evidence.
(d) Effectiveness and efficiency
In evaluating the effectiveness and efficiency of CAATs, the auditor should consider the benefit and costs of it.
(e) Timing
Certain computer files may be retained for a short period of time which may affect the timing of carrying out audit procedures. CAATs may be a solution for an audit assignment with a tight time constraint.
1.2.2 CAATs may be used during various audit procedures, such as:
(a) detailed testing of transactions and balances – use of audit software to test all or a sample of transactions in a computer file, for example.
(b) analytical procedures – use of audit software to identify unusual fluctuations or items, for example.
(c) testing of application controls – use of test data to check the functioning of a programmed procedure.
(d) testing of general controls – analyse logs and to review program library access procedures.
2. Categories of computer-assisted audit techniques
2.1 Test data
(a) Nature and purposes of test data
2.1.1 Test data techniques are sometimes used during an audit by entering data (e.g. a sample of transactions) into an entity’s computer system, and comparing the results obtained with predetermined results.
2.1.2 Test data is data generated by the auditor, which is then processed using the client’s computer systems.
2.1.3 The objective of test data is to ensure that the controls within the system are operating properly. If this is the case, then erroneous items should be rejected.
2.1.4 Consequently, test date should contain data of both a valid and an invalid nature. It may be processed during a normal production run (live test data) or during a special run at a point in time outside the normal cycle (dead test data).
2.1.5 An integrated test facility (ITF) (整體測試設施) requires the establishment of a dummy unit (e.g. department or employee) against which the auditor’s test data transactions are processed during the normal production cycle.
2.1.6 When test data are processed with the entity’s normal processing, the auditors ensure that the test transactions are subsequently eliminated from the entity’s accounting records.
(b) Use of test data
2.1.7 Auditors might use test data to:
(a) test specific controls in computer programs, such as on-line password and data access controls;
(b) test transactions selected from previously processed transactions or created by the auditors to test specific processing characteristics of an entity’s information systems. Such transactions are generally processed separately from the entity’s normal processing;
(c) test transactions used in an integrated test facility where a “dummy” unit is established, and to which test transactions are posted during the normal processing cycle;
(d) perform reasonableness checks on input by inputting transactions outside predetermined ranges;
(e) confirm exception reporting facilities by inputting a batch of transaction with known exceptions and comparing the exception report with the expected results;
(f) ensure that programmed controls work effectively;
(g) verify programme specification which includes programme control such as edit and validation checks;
(h) understand client’s application systems and related procedures.
(c) Precautions in apply test data
2.1.8 The precautions are described as follows:
(a) Test data should be run ‘live’ if possible. If not possible it is necessary to ensure that programs used are identical to or are the actual programs used by the client.
(b) Any fictitious items included as test data must be retrieved from files before the client uses those files in normal processing otherwise errors could be created by the auditor.
(c) If test data is to be run ‘dead’, there must be adequate computer time available, and the special run required must not prove unduly expensive.
(d) Since controls are being tested, all discrepancies between predicted and actual results must be fully resolved and documented, irrespective of financial amounts involved.
(d) Procedures to control test data applications
(Dec 10)
2.1.9 PN 1009 specifies the procedures to control test data applications that the auditor has to carry out:
(a) To control the sequence of submissions of test data when involving several processing cycles.
(b) To perform pilot runs containing small amounts of test data before submitting the main audit test data.
(c) To predict the results of the test data and comparing it with the actual test data output.
(d) To confirm that the current version of the programs was used to process the test data; and
(e) To test whether the programs used to process the test data were the programs the entity used throughout the applicable audit period.
2.2 Parallel simulation
(a) Nature and purposes of parallel simulation
2.2.1 A parallel simulation involves the auditor writing a computer program that replicates some part of a client’s application system. A tool commonly used by auditors to perform parallel simulation testing is generalized audit software, which is a software designed specifically for use by auditors.
2.2.2 The use of parallel simulation requires that the auditor construct a computer simulation that mimics the client’s production programs. With this method the auditor processes actual client data through the simulated program and compares the results with the client’s processing of that data. The lack of differences in output indicates effectively functioning client’s software, whereas differences indicate potential deficiencies.
(b) Advantages of parallel simulation
2.2.3 Parallel simulation is useful in the following areas:
(a) To facilitate the substantive testing of client account balances.
(b) To provide evidences on the controls used in the client’s application programs.
(c) To test the accuracy of large volumes of transactions.
(d) To emphasize exception helps auditor to focus on items where there are differences. Most parallel simulation applications are used to process the entire set of the relevant client data. While the parallel simulation can be design to sample client data, this is the exception rather than the norm.
(c) Disadvantages
2.2.4 The major issue is the cost of developing parallel simulations. The costs of developing the simulations may be higher than using generalized audit software for transaction testing because the cost of using parallel simulation depends on the part of the client’s system to be simulated, the complexity of the client’s calculations, and the amount of data to be processed.
2.3 Use of personal computer (PC) in auditing
2.3.1 Spreadsheets
(a) Prepare trial balance and lead schedule by extracting balances from the ledger accounts.
(b) Perform analytical procedures by extracting balances of financial statements and then calculate financial ratios and compare with prior year’s balances.
2.3.2 Word processors
(a) Prepare standard audit documentation such as accounts receivable confirmation control schedule, standard audit program, etc.
(b) Document client’s internal control system including preparing narrative description, flowcharts and internal control questionnaire.
2.3.3 Data extraction software
(a) Retrieve and analyze data downloading data from client’s computer files and putting into working papers for further analysis and testing.
(b) Prepare statistical sampling including the design of sampling application and select the sample items.
3. Generalized Audit Software (GAS)
3.1 Nature and purposes of GAS
3.1.1 GAS includes programmes that allow the auditor to perform test on computer files and databases. Generalized audit software is the generalized programs designed to:
(a) read computer files
(b) select information
(c) perform calculations
(d) create data files
(e) print reports in a format specified by the auditor
3.2 Function of GAS
3.2.1 The auditor can potentially perform many different types of tests; these include the following:
Functions |
Explanation |
1. File or database access |
|
2. Arithmetic functions |
|
3. Statistical analysis |
|
4. Report generation |
|
5. Examine records |
|
6. Compare data on separate files |
|
7. Select audit samples |
|
8. Print confirmation requests |
|
3.3 Advantages of GAS
3.3.1 Advantages:
(a) GAS are developed in such a manner that most of the audit staff can be trained to use the program even if they have little formal computer education.
(b) Limited IT expertise or programming skills are required for using GAS.
(c) This is a single program that can be applied to a wide range of tasks without having to incur the cost or inconvenience of developing individualized programs.
(d) The time required to develop the application is usually not too much.
(e) GAS can be applied to wide variety of clients with minimal customization.
3.4 Disadvantages of GAS
3.4.1 Disadvantages:
(a) The high initial cost of their development and their relatively inefficient processing speed.
(b) It provides a limited ability to verify programming logic because its application is usually directed to testing client files or databases.
(c) It involves auditing after the client has processed the data rather than while the data is being processed.
4. Types of Computer Packages
4.1 The person responsible for developing and acquiring computer packages should identify what the users need, and how those needs can be satisfied. There are three basic alternatives that the analyst may consider:
(a) bespoke software (定制軟體);
(b) general purpose package
(c) off-the-shelf package (現成軟體)
4.2 Bespoke systems approach
4.2.1 Bespoke systems approach (or tailor-made systems) are designed to fit the specific needs of the organization. They may be produced in-house, or commissioned (委托制作) from an outside software company.
4.2.2 Advantages
(a) they should precisely fit the organization’s information needs;
(b) the organization has complete discretion over data structures;
(c) the system can be integrated with other applications within the organization;
(d) the system can be modified to fit changing needs.
4.2.3 Disadvantages
(a) development takes a long time;
(b) costly to develop and test;
(c) greater probability of bugs;
(d) supporting is expensive.
4.3 General purpose packages approach
4.3.1 General purpose packages (or software package) approach can provide approximate solutions to a range of different problems. Many such packages can be tailored so that they can be adapted to fit a specific solution.
4.3.2 Advantages
(a) less expensive than bespoke;
(b) available more quickly than bespoke;
(c) likely to be a number of people with expertise in the relevant package;
(d) training and documents likely to be readily available;
(e) can be used for a number of different applications;
(f) can be used as prototypes (樣板,模范) for bespoke systems;
(g) the package is a proven product that has undergone systems testing (in development) and user acceptance testing (by the users who have already bought and used the package).
4.3.3 Disadvantages
(a) may not fit the information needs of the organization as well as a bespoke package;
(b) have to adapt itself to the limitations of the package;
(c) data must be structured to fit the requirements of the package.
4.4 Off-the-shelf approach (Ready-made software)
4.4.1 Off-the-shelf packages are software solutions purchased from a software vendor and used without any amendments in the organization.
4.4.2 Advantages: (Jun 09, Jun 13, Jun 14)
(a) generally much cheaper to buy than bespoke packages;
(b) likely to be available almost immediately;
(c) system bugs should have been discovered by other users and eliminated;
(d) new updated versions of the software are likely to be available on a regular basis;
(e) the experience of a great number of users with similar needs to those in the organization has been incorporated into the design of the package.
4.4.3 Disadvantages:
(a) not fit precisely the needs of the organization;
(b) dependent on an outside supplier for the maintenance of the software;
(c) may have incompatible data.
(d) does not have full control of system once the package is purchased.
5. Outsourcing
(Jun 09, Jun 15)
5.1 Outsourcing involves the transfer of the management and/or day-to-day execution of an entire business function to an external service provider.
5.2 The following list of services is a fair representation of the kinds of services that a typical IS function will place contracts for:
(a) training on packaged software
(b) maintenance of hardware
(c) operating system support
5.3 Advantages:
(a) cost savings;
(b) improved quality with the expertise provided by suppliers;
(c) flexible in resources deployment;
(d) the release of managers to concentrate on other activities.
5.4 Disadvantages:
(a) Loss of control – the dependency on supplier and the company loss its own skills to deal with IT problems;
(b) Being tied to one system – high switching cost dependent on the terms of contracts;
(c) Risk of confidentiality – if information systems are a core competence then they must not be outsourced; then it is possible that the company may loss competitive advantage in the market place. On the other hand, trade secrets or proprietary information may leak out to competitors or confidential data may be shared with others.
6. In-house programmer
(Jun 09)
6.1 Advantages:
(a) Compared with off-the-shelf (ready-made):
(i) Tailor-made software
(ii) Strong communication between in-house programmer and the staff. The in-house programmer can modify the software according to the needs of the company.
(iii) More flexibility to change. For example, the programmer can update software for the discount policy, and manual input by shop managers is no longer required. Business processes are being carried out efficiently and effectively with a fast turnaround time.
(b) Compared with outsourcing:
(i) Faster response if only one set of systems breaks down.
(ii) Higher confidentiality as technician is an in-house staff member.
Source: https://hkiaatevening.yolasite.com/resources/PBEAuditNotes/Ch21-CAAT.doc
Web site to visit: https://hkiaatevening.yolasite.com
Author of the text: indicated on the source document of the above text
If you are the author of the text above and you not agree to share your knowledge for teaching, research, scholarship (for fair use as indicated in the United States copyrigh low) please send us an e-mail and we will remove your text quickly. Fair use is a limitation and exception to the exclusive right granted by copyright law to the author of a creative work. In United States copyright law, fair use is a doctrine that permits limited use of copyrighted material without acquiring permission from the rights holders. Examples of fair use include commentary, search engines, criticism, news reporting, research, teaching, library archiving and scholarship. It provides for the legal, unlicensed citation or incorporation of copyrighted material in another author's work under a four-factor balancing test. (source: http://en.wikipedia.org/wiki/Fair_use)
The information of medicine and health contained in the site are of a general nature and purpose which is purely informative and for this reason may not replace in any case, the council of a doctor or a qualified entity legally to the profession.
The texts are the property of their respective authors and we thank them for giving us the opportunity to share for free to students, teachers and users of the Web their texts will used only for illustrative educational and scientific purposes only.
All the information in our site are given for nonprofit educational purposes